Port Forwarding from WSL2 (Guest) to Windows (Host) Machine
It’s been quite a while since my last medium article. At the moment, I’m having my OffSec AWAE Lab in preparation of OffSec Web Expert…
It’s been quite a while since my last medium article. At the moment, I’m having my OffSec AWAE Lab in preparation of OffSec Web Expert (OSWE) certification. Since it is recommended to use Kali Linux while doing the labs, I feel lazy booting up my VMWare. Hence, using WSL2 is a good shot for me. However, on some lab scenarios it is mandatory to run services that do not exist (or rather took so much effort to install) in Windows such as impacket-smbserver or any Kali Linux exclusive tools. It is such an ease anyway to use the tools that natively running on Linux distribution rather than “forcing” it to be run on Windows. This is where the solution comes: ✨Port Forwarding✨
Check your guest machine IP using ip a (abbreviation of address)
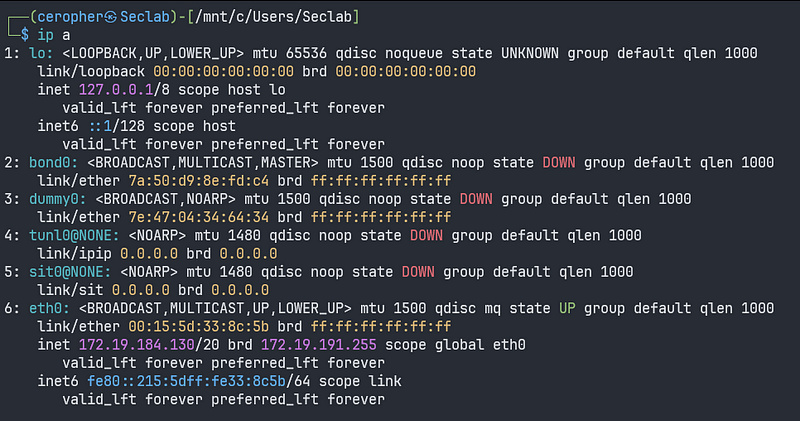
eth0 will be the interface to be forwarded from WSL2. Now, check your host machine IP using ipconfig
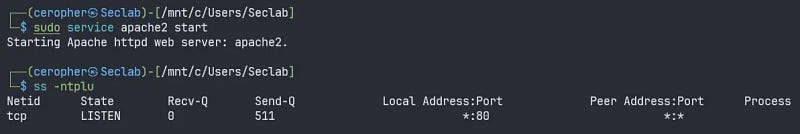
In this case, I’m going to forward port 80 on guest machine to be accessed on any interface (specifically my OpenVPN interface) on host machine. We see that the apache2 service has been started on port 80
Save this PowerShell code as network.ps1
param (
[Parameter(Mandatory = $true)]
[int[]]$p
)
If (-NOT ([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator")) {
$arguments = "& '" + $myinvocation.mycommand.definition + "'"
Start-Process powershell -Verb runAs -ArgumentList $arguments
Break
}
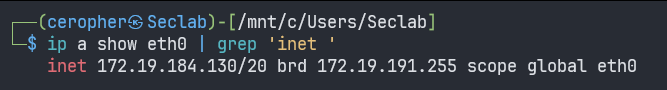
$remoteport = bash.exe -c "ip a show eth0 | grep 'inet '"
$found = $remoteport -match '\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}';
if ($found) {
$remoteport = $matches[0];
} else {
Write-Output "IP address could not be found";
exit;
}
for ($i = 0; $i -lt $p.length; $i++) {
$port = $p[$i];
Invoke-Expression "netsh interface portproxy delete v4tov4 listenport=$port";
Invoke-Expression "netsh advfirewall firewall delete rule name=$port";
Invoke-Expression "netsh interface portproxy add v4tov4 listenport=$port connectport=$port connectaddress=$remoteport";
Invoke-Expression "netsh advfirewall firewall add rule name=$port dir=in action=allow protocol=TCP localport=$port";
}
Invoke-Expression "netsh interface portproxy show v4tov4";The script basically accepts parameter p as a list of ports, and requires the script to be run as administrator. It is then get the eth0 interface and grep the valid IP address that nears an inet word using regex.
The list of ports then iterated and put into some netsh commands along with the IP address. Those netsh in a nutshell:
netsh interface portproxy delete v4tov4 listenport=$port=> deletes any existing port proxy for the specified listen port.netsh advfirewall firewall delete rule name=$port=> deletes the existing firewall rule for the current port.netsh interface portproxy add v4tov4 listenport=$port connectport=$port connectaddress=$remoteport=> adds a new port proxy entry that listens on the specified port and connects to the remote IP address.netsh advfirewall firewall add rule name=$port dir=in action=allow protocol=TCP localport=$port=> creates a new firewall rule to allow incoming TCP traffic on the specified port.netsh interface portproxy show v4tov4=> displays the current port proxy configuration, showing the active entries.
Run PowerShell as Administrator. Run the previous script with additional -p flag for any forwarding ports.
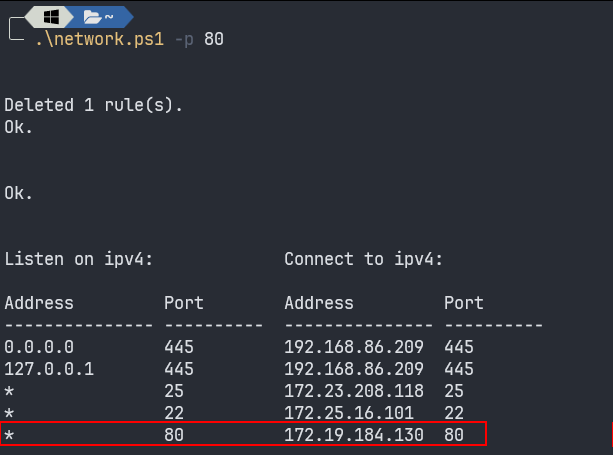
.\network.ps1 -p 80Port 80 on WSL has been successfully forwarded to Windows. Let’s check the corresponding port using:
netstat -ban | sls ":80"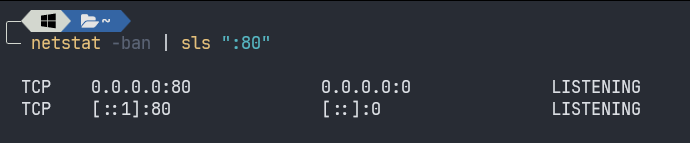
Since it is running on all interface, check if it is running on any interface on our Windows machine.
From this point, we can no longer booting up VMWare and use Kali Linux on WSL2 instead for all native services. Happy hacking~